
- Resources
- Blog
Can eSIM Help Resolve the IoT Security Headache?
Mobile Network Operators (MNOs), service providers, and cellular module makers are right to double down on M2M security, especially when you consider that both GSMA Intelligence and PSA Certified have released reports recently highlighting the scale of the challenge presented by IoT security. But the growing number of in-house (proprietary) solutions results in fragmentation. This disjointed approach to security only amplifies ongoing concerns over cost, knowledge gaps and lack for streamlined implementation.
IoT security is seen as important, but not many know how to achieve it
It won’t surprise you to hear that while the studies were carried out in isolation, both found that security was the criteria that sat at the top of most IoT decision maker’s lists. Nor will it come as a surprise to hear that 54% of respondents to the PSA’s survey found the cost of implementing secure IoT measures to be prohibitive. The reason for this prohibitively high cost could be due to the 76% of respondents believing there is a shortage of cyber security skills in their organization*. Accordingly, Symantec’s Security Summary June 2020 cites ‘A disjointed and siloed tool landscape along with a workforce sorely in need of training when it comes to cyber security skills and best practices.’



Of course, we should invest in better toolchains and talent. After all, Benjamin Franklin said, “An investment in knowledge pays the best interest”. But what if that investment is needed right now and is expensive? It results in either unsecured devices being deployed, or your organization missing out on the IoT gold rush thanks to those high barriers to entry. Knowledge of security by design is a skillset that’s in high demand, scarce and expensive. As a result, the investment in obtaining it and baseline security is often traded off against value added features. It’s a stark decision, but some device manufacturers make the daily choice to invest in differentiation over foundational security.
Newsletter Sign-up// – Light Gray Inline
Sign-up for our newsletter to receive the latest from Kigen.
“We see devices in the market without a baseline of security, lacking best practice implementation – paired with growing hacks, fragmentation of standards, and a fast uptick in device shipments. This leaves a glaring gap between where we are now and where we need to be. These are the challenges we need to solve and bridge, but also opportunities in the making.” PSA Certified Security Report 2021
We found a shortcut – but proceed with caution…
We have a skills gap to fill, but we lack the time and resources to plug it, so there must be another way. Franklin also noted that “Out of adversity comes opportunity”, and it comes in the form of a standardized root of trust (RoT) – a means of addressing some of this costly skills gap while instilling security and reducing fragmentation. All of the reports mentioned here agree that a root of trust is a crucial part of achieving end-to-end device security. It provides a set of unconditionally trusted functions that the rest of a system can rely on to enforce device security. By separating the data gathered during the device’s operation, from system software and firmware, a RoT can ensure that it remains confidential and impervious to software attacks.
The RoT handles critical functions like trusted boot, cryptography, attestation, and secure storage that are key to authenticating devices, verifying it remains uncompromised and any data gathered or transmitted has integrity and is encrypted. It provides a scalable solution for a device’s authentication with the cloud, as well as ensuring confidentiality during data exchanges and updates.
But the growing number of different RoT implementations, together with the fragmented hardware and operating system choices, present a great challenge to organizations. They grapple with connecting various disparate applications and protocols and struggle to stay ahead of the constantly evolving threats to a device during its life cycle.



The RoT landscape is only going to become more complex as the IoT space grows and new entrants offer more choice to the ecosystem and complexity stands in the way of scalability, which sounds remarkably like the situation we were trying to avoid. Romil Bahl – CEO of KORE Wireless – commented on the complexities in our recent webinar ‘Solving the IoT’s Trust Conundrum and Achieving the Promise of the IoT’:
“The industry has not been kind to those wishing to adopt IoT and the onus was on the deploying company to put the pieces together”.
In the webinar, Romil highlights how he spent his early days with KORE C-level executives who were scratching their heads over componentry rather than value proposition:
“I realized we needed to simplify IoT. The fragmented ecosystem feeds into that, with a McKinsey study finding you need an average of 18 partners to launch one IoT solution. You’ll need to talk to 100 companies to get down to selecting 18 partners. That’s far too many. Organizations need a one-stop-shop across connectivity, solutions and analytics.”
Buy off the shelf
The skills gap becomes even more critical when the industry struggles with componentry complexity and the GSMA Intelligence report cites IoT complexity as the biggest threat to security. But this can be resolved by simply adding the IoT SAFE application to your preferred SIM form factor, to act as a root of trust in a standardized manner. Standardization comes in the form of IoT SAFE specifications which we have covered earlier in relation to iSIM.



However, using eSIM is an approach that is garnering favour with 85% of enterprises responding to GSMA intelligence’s report indicating eSIM as necessary in realizing their digital transformation. Why? eSIM leverages existing SIM infrastructure and follows an interoperable industry standard, reducing the burden on developers to keep writing code and individually fathoming security mechanisms with individual suppliers.
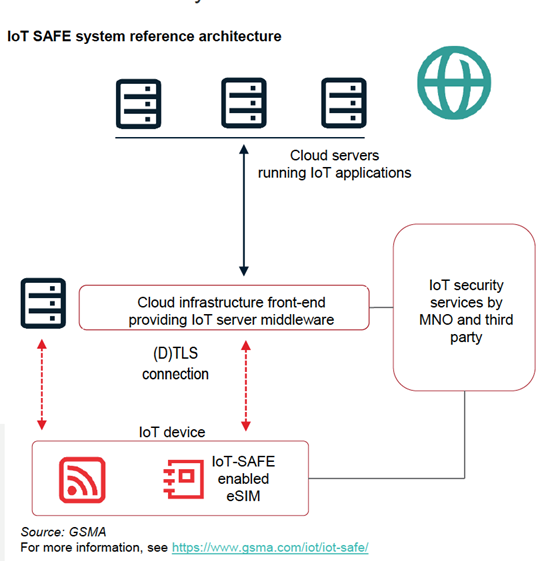


eSIM is becoming the form factor of choice for module makers looking to instill a root of trust in their devices. Combining it with the GSMA-led IoT SAFE standard represents the single most significant step a module maker can take in realizing robust, scalable chip-to-cloud security. By standardizing the proprietary, fragmented operating systems and protocols, enterprises can bring secure, scalable IoT to market sooner.
You can view the webinar on-demand here.



