
- Resources
- Blog
Securing IoT in a 5G world: new approaches for innovation
This article was originally published in Business Reporter on 28th of April 2021. Republished with permission.
Cellular IoT’s ubiquitous connectivity is a key draw for engineering innovations across fast-growing markets such as infrastructure for more intelligent transport, smart consumer services, smart city devices and connected health. The adoption of 5G is going to significantly accelerate the deployment of these connected devices. But as with most disruptive new technology waves, 5G brings its own challenges that require designers to consider how they support new radio bands while balancing not making IoT device design too complex. Increasingly, the devices in question are low-power, long-lived in the field and low cost; afford low levels of physical access; and are deployed across further and remote locations.
Cellular IoT has long been the choice of secure, large-scale and resilient deployments due to the robust subscriber identity module (SIM) that authenticates a device. As our devices shrink, and as remote devices must endure a wider range of environmental conditions, securing the device’s identity requires new and broader solutions.
Every connected device will need to be updated at some point throughout its lifespan. One of the advantages of IoT devices is that they can receive software and firmware updates over the air. That said, the ability to only allow authorized updates is critical to ensuring the integrity of the device and the code running on it.
Scale is both the IoT’s most significant opportunity and hurdle. Manufacturers need to consider how they will manage and secure the device throughout an extended lifecycle – in the case of cars and even consumer devices, this includes an ‘after-sales’ business model to support the ability to repair, replace or decommission securely to be more sustainable.
Introducing the eSIM
Embedded SIM (eSIM) technology is still a hardware-based SIM, but this elegant, robust and scalable technology is soldered permanently into the device and was designed to address some of the challenges impeding true scalability in cellular IoT. eSIM allows devices to be deployed anywhere with existing cellular coverage; operator profiles or network providers can be updated over the air, based on standards that offer a frictionless experience for device manufacturers and service operators.
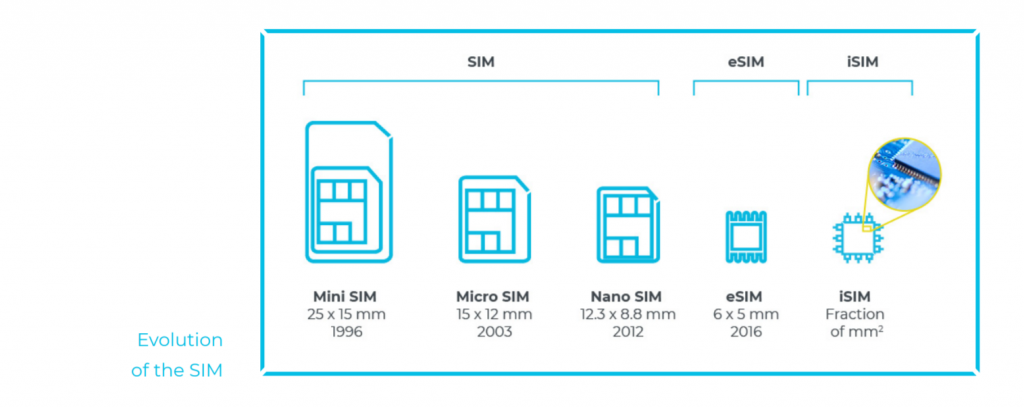


iSIM builds upon eSIM
But there’s more: an integrated SIM (iSIM) takes all the benefits of a standards-compliant eSIM and embeds them into the device’s permanent hardware array by combining the SIM with the system-on-a-chip architecture and cellular modem. Fusing the secure locations into the chipset itself offers a low footprint and introduces extra layers of security through a hardware-based secure enclave (a dedicated processor for security operations) that maintains the integrity of all cryptographic and key managed operations.
Newsletter Sign-up// – Light Gray Inline
Sign-up for our newsletter to receive the latest from Kigen.
Security and scale go hand in hand
As the number of devices ramps up, the IoT attack vector will grow exponentially, and security cannot be an afterthought. IoT continues to move closer to core processes, and businesses should ensure that both devices (i.e. the endpoint itself) and data exchange (in technical terms, the chip-to-cloud security) have strong identity and trust foundations.
To achieve scale, businesses need simpler ways of manufacturing while being able to keep the robust security benefits derived from SIM capabilities. This has typically proven to be a challenge as new market needs for IoT are emerging. The fastest growth of eSIM and iSIM deployments is coming from markets that have not traditionally operated at the same cost points as the cellular or smartphone industry. Markets such as fleet management of e-bikes or e-scooters or connected health wearables did not exist in their current capabilities a few years ago.
Within these, businesses need simplification of both the bill of materials and that of the supply chain. iSIM fundamentally changes the way device makers can access cellular capabilities for devices that could not be served before. iSIM offers the highest protection for subscription credentials and isolates processing in a secure enclave. An additional authentication layer serves as a root of trust for secure communications while reducing the bill of materials.
One of the often-overlooked elements of security design is how trust is granted to a device and managed throughout its lifecycle. While trust is relatively easy to manage within a trust manufacturing environment, it is much more difficult once that device leaves the factory floor.
The GSMA standard IoT-SAFE iSIM supports the entire secure chip-to-cloud IoT infrastructure. It allows iSIMs to authenticate both connectivity and application credentials for any data being exchanged with any cloud over any cellular network by any device.
New opportunities
eSIM and iSIM are solutions to existing problems, but they also open up new opportunities for broader innovations. Artificial intelligence (AI) and machine learning (ML) have an increasingly important role to play in the IoT. The Economist Intelligence Unit reported in 2020 that 90 per cent of companies with extensive IoT deployments link their real-time data gathering with their AI planning. Companies with mature deployments can justify the traditionally high cost of incorporating AI and ML, as they had a demonstrable ROI from an existing deployment.
Luckily, that barrier to entry is being lowered today and we’re seeing the cost of leveraging these tools falling, broadening the types of diversity of devices that can be intelligent nodes across low-power, wide-area networks working together with mainstream 5G networks. Massive IoT will support the mainstay applications that we have come to envision with 5G, such as cellular-to-vehicle-to-everything (C-V2X).
The use cases are as broad as they are attractive. eSIM and iSIM are paving the way for centralisation of agricultural operations as smaller, less expensive tracking devices can be deployed in remote, extreme environments, and global logistics providers can track more assets in real-time with low-power secure modules that go for months between charges. The opportunities presented by cellular IoT underpinned by 5G are abundant. Herein is represented an unprecedented opportunity for collaboration across manufacturing, engineering, commerce and technology providers to ensure the 5G digital economy has security as its cornerstone.
You can view the article here.



